Make Cybersecurity Easier with Bulk IoC Importing into Microsoft Defender for Endpoints

Step-by-Step Instructions for Importing IoCs:
1. Log in to Microsoft 365 Defender:
- Go to the Microsoft 365 Defender portal at security.microsoft.com and log in with your administrator credentials.
2. Access the Indicators Section:
- Navigate to Settings -> Rules -> Indicators. This section allows you to manage and upload IoCs such as file hashes, IP addresses, URLs, and domain names.
3. Download the CSV Template:
- In the Indicators section, click on the Import button and select Download sample CSV. The template contains required fields for each IoC type. Refer to the template to ensure your CSV file follows the correct structure.
4. Prepare Your CSV Files:
- Based on the type of IoCs (e.g., file hashes, URLs, IP addresses, or domain names), structure your CSV file accordingly. Below are examples from your files:
For URLs:
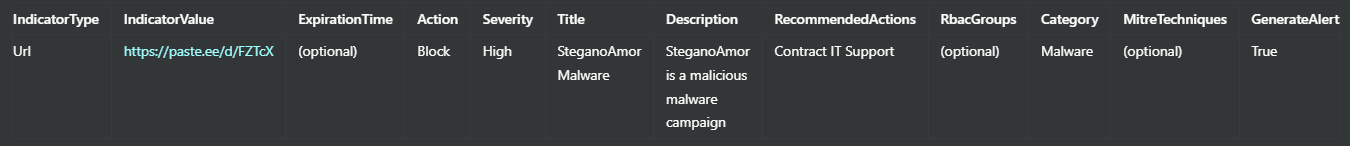
For File Hashes (SHA-256):
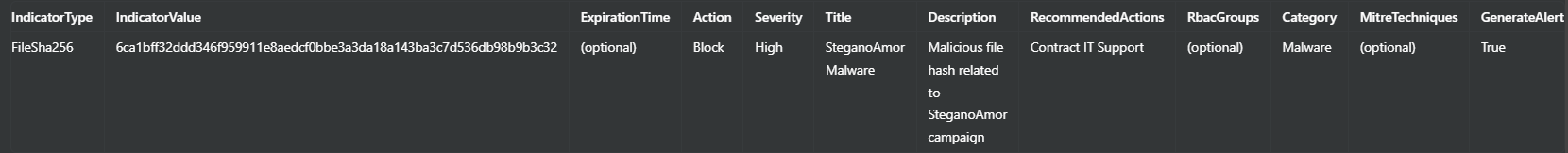
For IP Addresses:
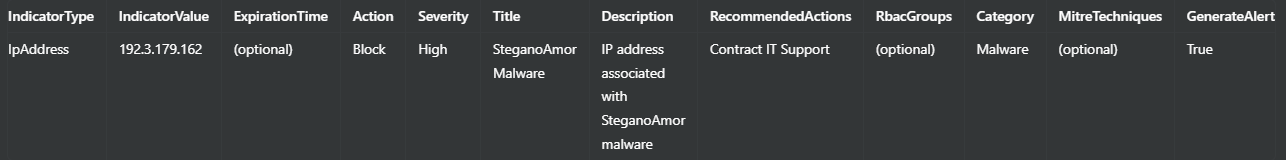
For Domains:
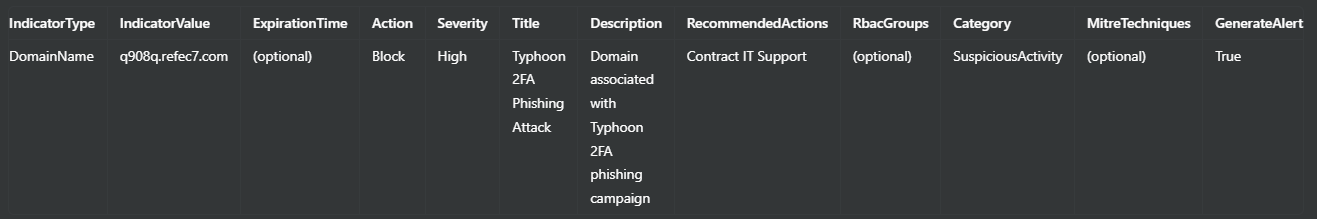
Example of a Bulk Import CSV:
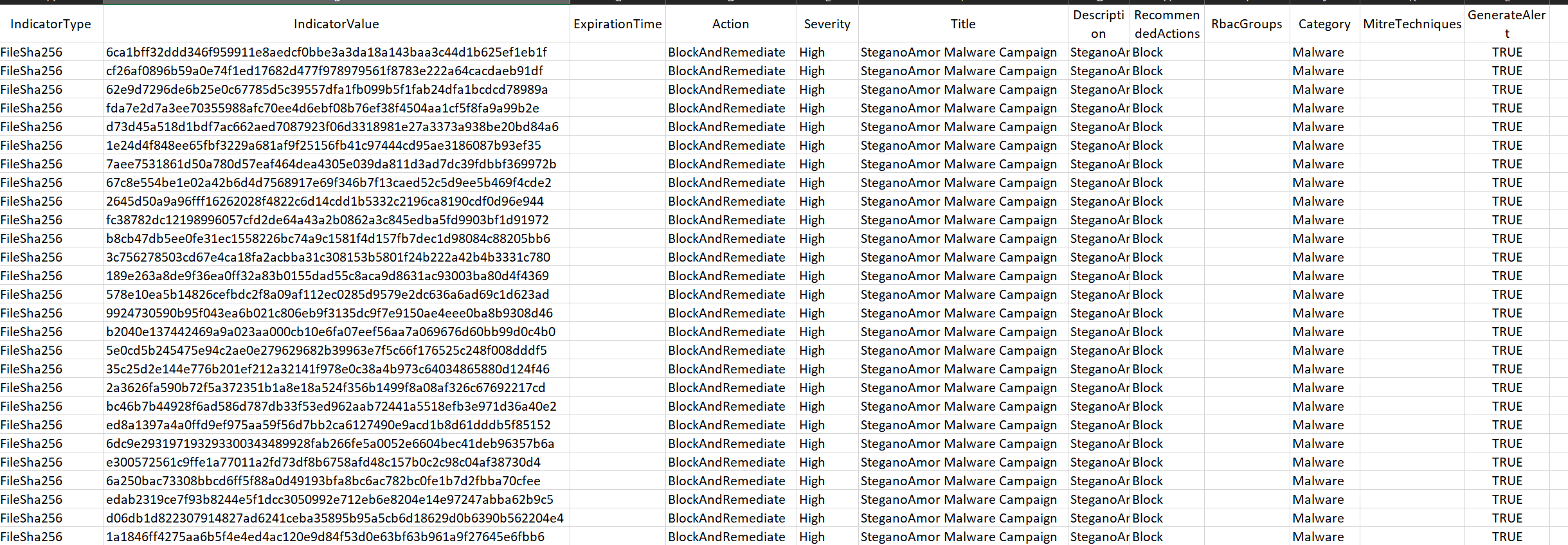
- Ensure each CSV file is saved with a unique name and retains the
.csvextension.
5. Upload the CSV Files:
- In the Indicators section, click Import and select CSV as the file format. Drag your prepared CSV file or browse to locate it on your system.
- Choose how to handle invalid entries:
- Import only valid indicators.
- Reject the entire file if there are any invalid indicators.
6. Monitor the Import Process:
- After uploading, go to Manage file imports to check the status. This section will list any errors found in your CSV file and allow you to download an error report. You can fix errors and re-upload the file if necessary.
7. Verify the Imported IoCs:
- Once the import is successful, you can see the imported IoCs under the corresponding categories (e.g., URLs, file hashes, IP addresses, domains). Verify that they are listed with the correct actions (e.g., Block, Allow).
Tips:
- ExpirationTime is optional but can be used to specify when the IoC should expire.
- Always review the Action field to ensure that it reflects your desired outcome (e.g., Block, Allow).
- The Severity field should reflect the level of threat (e.g., High, Medium, Low).
- Ensure the GenerateAlert field is set to
Trueif you want alerts triggered for the specified IoCs.


